SIR Trading Exploit: DeFi Protocol Loses Entire $355K TVL, Places Bounty on Attacker of $100K
Key Takeaways:
- Overall Loss: Ethereum-based DeFi protocol SIR.trading was affected by a significant exploit that led to it losing its entire Total Value Locked (TVL) worth approximately $355,000.
- Bounty Offer: The creator of the protocol, Xatarrer, offered a bounty of $100,000 to the attacker as an incentive to return the balance of funds in exchange, exemplifying the development of the project by the community and lack of venture capital support.
- Exploit Explanation: The exploit took advantage of problems with the temporary storage used by Ethereum, a temporary data storage during transaction execution.
Loss of All the Funds in SIR.trading Exploit
SIR.trading, an Ethereum-based decentralized finance (DeFi) protocol, suffered a devastating exploit that saw it lose its entire Total Value Locked (TVL) of approximately $355,000. The protocol attack on March 31 drained the protocol’s funds completely, and the developers and users were left baffled for an exit.
The project’s anonymous developer, Xatarrer, then reached out to the hacker via on-chain message, acknowledging the maturity of the exploit and promising to give a $100,000 bounty if the stolen money is returned.
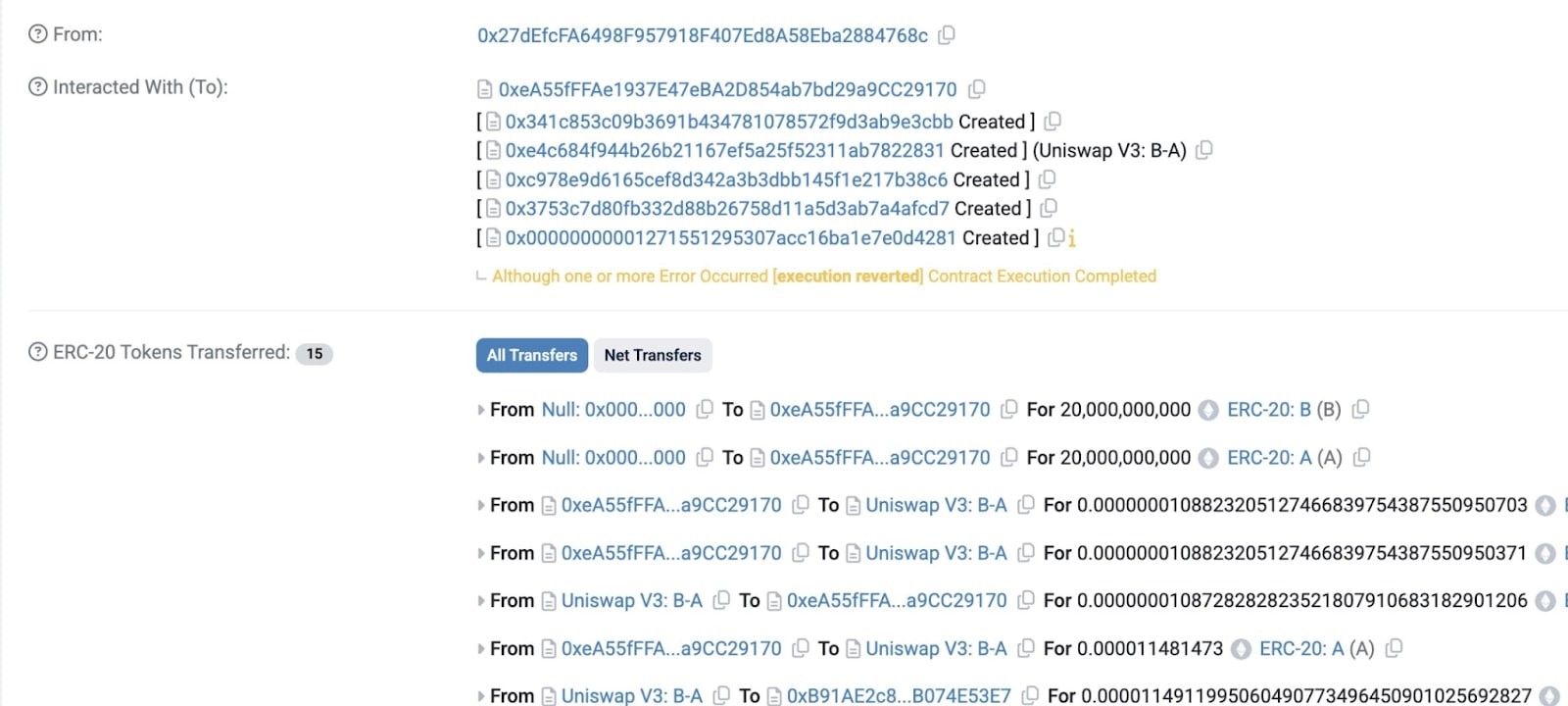
SIR.trading Exploit – Blockchain Transaction Attack
Bounty Offer and Developer’s Response
Following the attack, Xatarrer publicly addressed the attacker, offering a reward of $100,000 as a “fair share” for discovering a serious flaw in the protocol. The developer went on to explicitly confirm that no legal proceedings would be taken should the remaining funds be returned.
The reward offer is part of a trend within DeFi, where developers attempt to negotiate with the attackers rather than resort to legal means. Previous attempts have yielded mixed results, with some attackers returning part of the stolen funds while others do not wish to speak.
Exploit Mechanism: Ethereum Transient Storage Vulnerability
The attack exploited a vulnerability in Ethereum’s transient storage, an advanced feature that holds data temporarily as transactions are processed. While transient storage can boost efficiency, poor implementation can expose security flaws that can be abused by attackers.
Similar DeFi Exploits and Bounty Examples
This attack is one of a series of DeFi attacks that continue to reveal security vulnerabilities in decentralized applications. Other protocols have been in similar situations and tried to negotiate with hackers by providing bounties in return for stolen funds.
- Another DeFi protocol, Sturdy Finance, was attacked and provided a $100,000 bounty to the hacker if the stolen assets were returned.
- Euler Finance, losing nearly $200 million in an exploit, negotiated and was successful in recovering much of the funds through negotiations with the attacker.
- Curve Finance also faced an exploit, leading to an on-chain negotiation where hackers returned some of the funds after community pressure.
Security Measures and Risk Mitigation
To address growing DeFi attacks, security experts recommend that users and developers employ advanced tools to analyze and reduce risks. Security services such as DeFi offer security features, including:
- Shield – A vulnerability scanner that scans for vulnerabilities in smart contracts and identifies risk patterns.
- Scanner – Security analysis software that helps users analyze risk levels before interacting with DeFi protocols.
- Revoke Tools – Allow users to retract smart contract approvals, reducing exposure to potential attacks.
These security utilities allow DeFi users to find high-risk contracts, revoke potentially malicious approvals, and block malicious transactions.
Despite security measures, DeFi is an inherently risky ecosystem, in which even thoroughly audited smart contracts are made the subject of advanced attacks. The SIR.trading hack is a reminder of the requirement for ongoing security research and ongoing vulnerability testing.
Community and Market Reactions
The larger DeFi community reacted in both concern and skepticism following the SIR.trading exploit. A few security experts praised the developer’s integrity and attempt at negotiation, although others criticized the lack of security audits beforehand and questioned the value of offering a bounty.
DeFi security professionals also pointed out that attackers generally don’t have much to gain from returning their stolen funds, especially if they have already successfully laundered the assets through anonymity-promoting protocols like Tornado Cash.
Affected users complained, and many referenced the risks involved in investing in lesser, un-audited DeFi protocols. It is a reminder that even highly backed projects such as this one remain vulnerable if security vulnerabilities are not addressed appropriately.
More News: THORChain Under Fire as Swap Volumes Surge From Aftermath of Bybit Hack
The post SIR Trading Exploit: DeFi Protocol Loses Entire $355K TVL, Places Bounty on Attacker of $100K appeared first on CryptoNinjas.
CryptoNinjas



















